We are tagged with the identity of our parents on the day we are born. Our birth certificate is our first identity document and it is used to identify who we are in various transactions. During our lives, we collect numerous other identity documents that are associated with us - passport, driver’s license, country UID, etc. But there’s a catch. These are helpful in the physical world only.
Do you wonder how your friend’s identify you in digital world? Confused? They recognize you by either your email-id, phone-number, or social-media-handles. There is something common between all of them - they are all prone to hacks that can lead to forged transactions on your behalf. An email received by anyone from your email-id is treated to be as sent by you. But is that really true in all cases? In today’s age, what’s the guarantee that every transaction that uses your identity might actually be initiated by you? Imagine this situation in the digital financial world - a breach like this can lead to huge losses.
The digital world uses mechanisms to prevent misuse of identity information by adding multiple layers of authentication typically known as multi-factor authentication (MFA) like one time passwords (OTP) where you receive as an SMS. There are also time based OTP generation apps which take responsibility of generating a password that is one time use only and expires quickly. As secure as they make us feel, SMS based OTPs don’t always work. There are Android applications that can read your SMSes and auto forward them to other numbers without you knowing. They don’t take the responsibility of proving that the password was indeed used by the intended user. There is a very serious problem concerning authorising fund transfers and authorising mission critical orders etc.
At Neebal, we are always up for a challenge to make demanding possibilities real for our clients and had been considering different ways to tackle the issue of financial security when we were introduced to FT42 Labs in early 2017. We knew we met the right partner and started working on making financial transactions more secure for all our clients right away. Together, we came up with a Enterprise IAM Solution that we named 𝝿-CONTROL and it aims at providing “proveable” consent for each transaction authorised by a user. It uses cryptographic algorithms and hyperledger based blockchain on massively scalable infrastructure that provides the highest grade of transactional security. The icing on the cake is that it comes as a software development kit (SDK) that embeds into existing apps and simplifies the user experience keeping the security features intact.
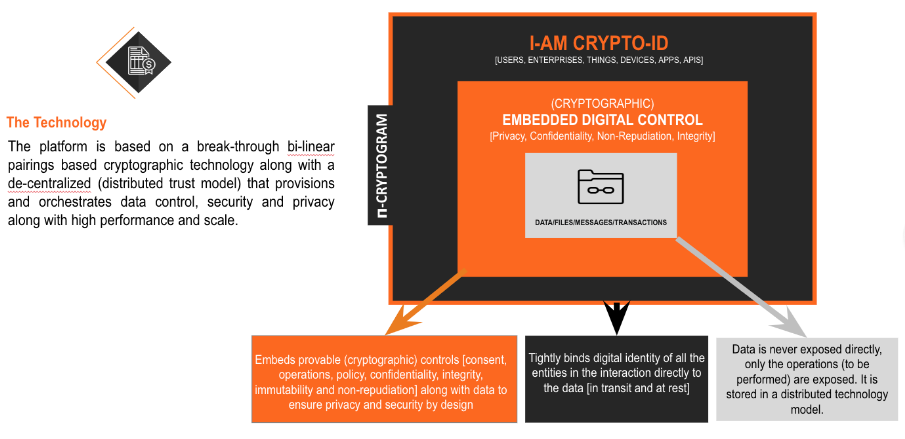
How 𝝿-CONTROL works
Over the last two years, we have helped our clients in the banking sector integrate the Enterprise IAM Solution with corporate banking transactions for their customers. We have secured identities for more than 1000+ enterprises and secured over 1M+ transactions in the past 12 months. We estimate that we will secure 60bn+ identities by 2025 with the advent of IoT, Cloud, Blockchain, and digital devices. Our solution safeguards identities of humans and systems alike. The unique design and massively scalable cryptography ensure we can secure identities and transactions across all participating digital entities, be it humans, enterprises, applications or things.
So, the question to ask yourself is are you in control of your identity? How secure are your transactions and data?
If you would like a quick security assessment of your systems and safeguard them from unauthorized transactions, reach out to me at vijay@neebal.com. Our team will perform a complimentary assessment and provide a detailed solution on how we can help safeguard your data & transactions.
